Reading Time : 1 Mins
A Quick Overview Of Application Security Testing For Agile Projects
An INFJ personality wielding brevity in speech and writing.
Software professionals in Finland were polled about their adoption, implementation, and opinion on 40 standard security testing practices and 16 agile software development tools, methods, and processes. Since then, a quantifiable impact has been observed on security engineering practices, thanks to adopting agile tools and procedures. A large majority (87%) of respondents had hands-on experience working on an agile-managed software development project that included security concerns.
Agile does not mention security, and customers have raised concerns about it in the past. It’s easy to imagine a scenario in which an application fulfilled all customer’s needs but also enclosed significant security vulnerabilities because security was probably not a top priority.
Since, nowadays, the application has customer data and sensitive information in store, it will likely remain on the radar of cybercriminals. The traditional approach of application security testing couldn’t guarantee 360-degree security. As a result, the need for continuously monitoring the application to combat any challenge arises under Agile projects.
The quest for good application security businesses requires extensive testing across the development process. They also require a broader view of why application testing is so important.
What is Application Security Testing?
Application Security Testing (AST) works to identify the security flaw and limitations of an application that can be exploited by cybercriminals and may result in unwanted performance shortly. With business expansions, there is a rise in complex and integrated functions of an application which further results in underperforming testing activities. However, with the AST becoming fully automated, organizations are now using various application security tools.
Application Security Testing – The Traditional Approach
Application Security Testing is not just about preventing unwanted data breaches, class-action lawsuits, and penalties for non-compliance. It opens up new ways to ensure better prospects for innovation and efficiency.
Since security is crucial in any sense, the traditional approach is underperforming in doing the same. It used to take a humongous amount of time while performing security activities, from setting up deployment gates to communicating output to application owners. For instance, security testing for manual secure code review usually takes weeks, according to the application size. It further means that the considerable time limit and the need for application deployment can’t be a better fit.
Also, the traditional approach turns out to take even a longer time when it comes to remediation with reports. The reports contain all the findings and transfer sessions with hour-long knowledge to confirm that the developers understand the vulnerabilities entirely.
As a result, it calls for an agile testing solution that simultaneously achieves security, ensuring quality and time efficiency. The current development process needs application security activity to be lightweight and delivered in bite-sized chunks to ensure the same.
Application Security Testing – The Agile Way
Modern problems need solutions, and businesses must opt for modern approaches to explore innovative ideas and opportunities. Agile testing is a new approach as it emphasizes innovative solutions ensuring product quality and believes in saving more time and effort. Let’s find out in what ways an agile approach ensures the same.
Let’s all agree that no matter how diligently a developer studies secure coding, there will always be a mistake in the code that can be spotted only by a seasoned professional. Therefore, it is recommended that each team appoint an application security test with some expertise in the area of application security.
Application security testing is responsible for things like:
- When creating stories with a high priority on security, it’s best to work in pairs.
- Locating and reporting vulnerabilities in the system to its creators.
- Participating in discussions concerning the selection of libraries, the establishment of contracts with third-party systems, the creation of public APIs, etc.
- Facilitating the testing of security-critical stories by Quality Analysts.
Opting for A Risky Approach
Opting for a risky approach needs you to determine the level of risk your organization can consider taking. A risky approach guides decisions on how deep and broad security testing can go and what to identify. For instance, the usual web vulnerabilities like SQL injection and Cross-Site Scripting (XSS) are crucial for web applications but might not be for embedded applications. Therefore, an agile security activity must focus on high-risk findings in the highest-risk application components.
Secure Application and Automation
An automation approach is of great importance to ensure quick findings constantly. And agile ensures to provide the same with some provisions.
- When a particular security tool or testing strategy turns out to be a false alarm with a particularly susceptible type, avoid automated reporting of findings to development teams. It prevents them from getting overwhelmed with development activities and keeps their faith in security practice ensuring productivity.
- Focus on the most critical finding while an automated approach and ensure whether your tools can identify and categorize the findings accurately or not.
- To make the agile security approach as sequential as your agile development approach, ensure your automated scanning finds the lower risks as critical findings decrease.
Interpreting Findings Into Solutions
As soon as you identify the bugs, you need to take an approach that gets you to meet the solution. An ideal approach includes:
- Handle every bug in application security as you treat any other bug in agile development.
- Handle security considerations as non-useful requirements.
- Create automated tests to monitor security bugs just like usual bug regression tests.
Using issue trackers to file security bug tickets ensures a day-to-day integration with developer operations only to keep the development secure in the first place. As soon as you identify the bug, fix it and create a test case simultaneously to avoid its turning back again.
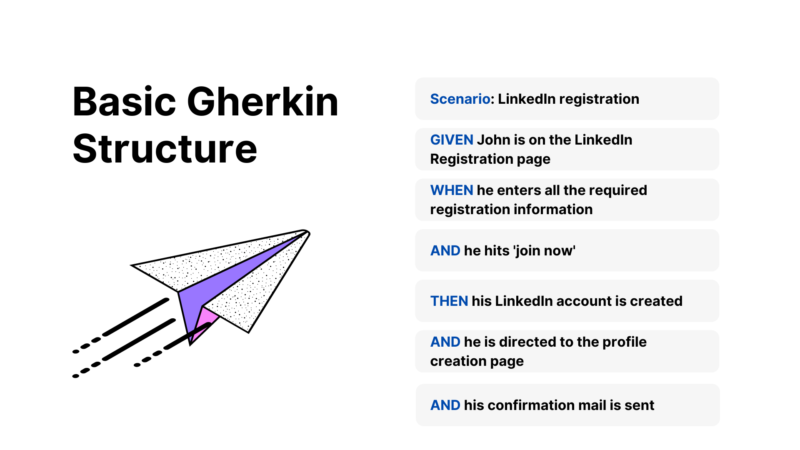
Conduct the test case activity using behavior-driven and test-driven tools and practices.
A snapshot of the BDD example:
Agile Testing Features
- Speed: Saving time for development teams is the biggest challenge while testing applications. It is what an agile testing approach ensures without losing the accuracy of the findings.
- Accuracy – more often than not, some security tools provide a false alarm that is undesirable. Agile testing ensures to act smart when identifying such scenarios.
- Automation – An ideal testing process needs a development team to conduct automated tests that can be scheduled daily, weekly, and monthly.
- Integration – A standard testing process offers a scenario where different security tools are integrated to get better results, ensuring an ideal testing development ecosystem.
Conclusion
It is evident that agile security testing ensures a time-efficient, satisfactory, flexible approach and prevents unwanted documentation. Businesses need to opt for robust, agile project developments if they aspire to stand out in their competition as credible ones. They need to ensure customers that their data is safe with them, and even if the business is transforming, the vision does not. To be effective in the long run, application security testing needs to be more agile as we advance into the future.
Looking to improve your product’s security posture? Take a look at Zuci’s security testing service and see how you can leverage Zuci for your business needs.
Related Posts






















